What Is Fraud Monitoring?
Fraud monitoring is the process of continuously scanning all account activity and transactions to identify signs of fraud. Modern, risk-based anti-fraud systems can analyze vast amounts of data to spot anomalies and flag those transactions.
To accomplish this, today’s most robust fraud monitoring solutions leverage statistical analysis and data models. By continuously feeding these models with data on legitimate and fraudulent transactions and interactions, algorithms can be trained to tell the difference between the two.
Using this approach, businesses can protect themselves and their brands from both common and emerging forms of fraud while preserving the customer experience.
Why Is Fraud Monitoring Vital?
As modern society moves to a more convenient, digital world, hackers have new opportunities to hack digital transactions. The US Federal Trade Commission states that more than 2.8M consumers reported losing over $5.8 billion to fraud in 2021. To compare, this is almost 70% more than the same indicator of 2020.
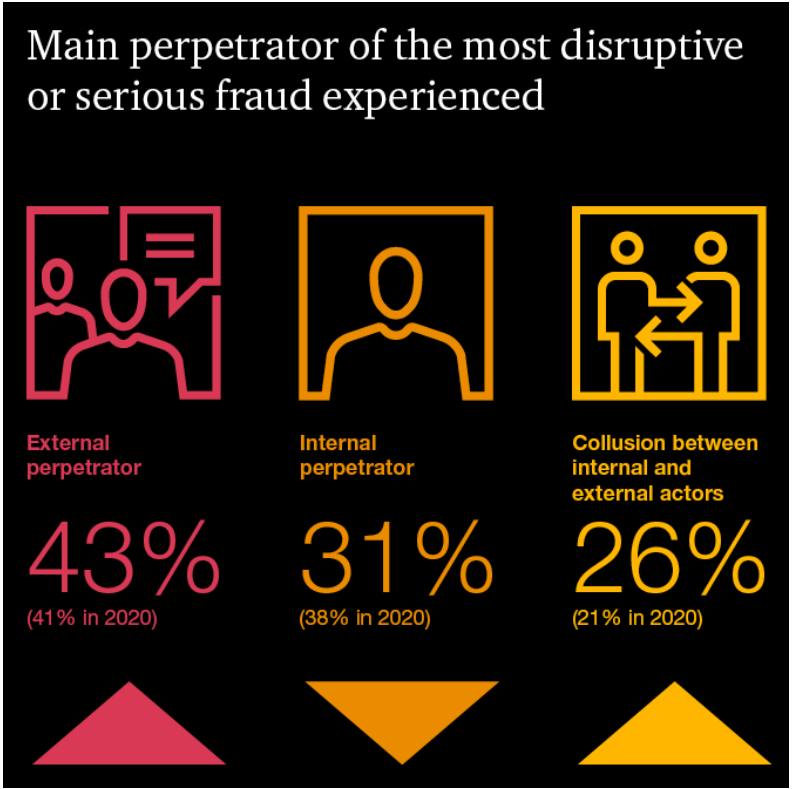
According to PwC, the main threat comes from external perpetrators. The results of the survey, conducted with 1,296 executives from 53 countries, showed that nearly 70% of organizations were affected by disruptive incidents coming from external attacks.
Source: PwC’s Global Economic Crime and Fraud Survey 2022
The number of fraud-affected people in 2021 is the highest on record, dating back to 2021. Estimations show frauds make victims lose $500 on average. Here is why fraud monitoring is no longer a novelty but a necessity for businesses and organizations.
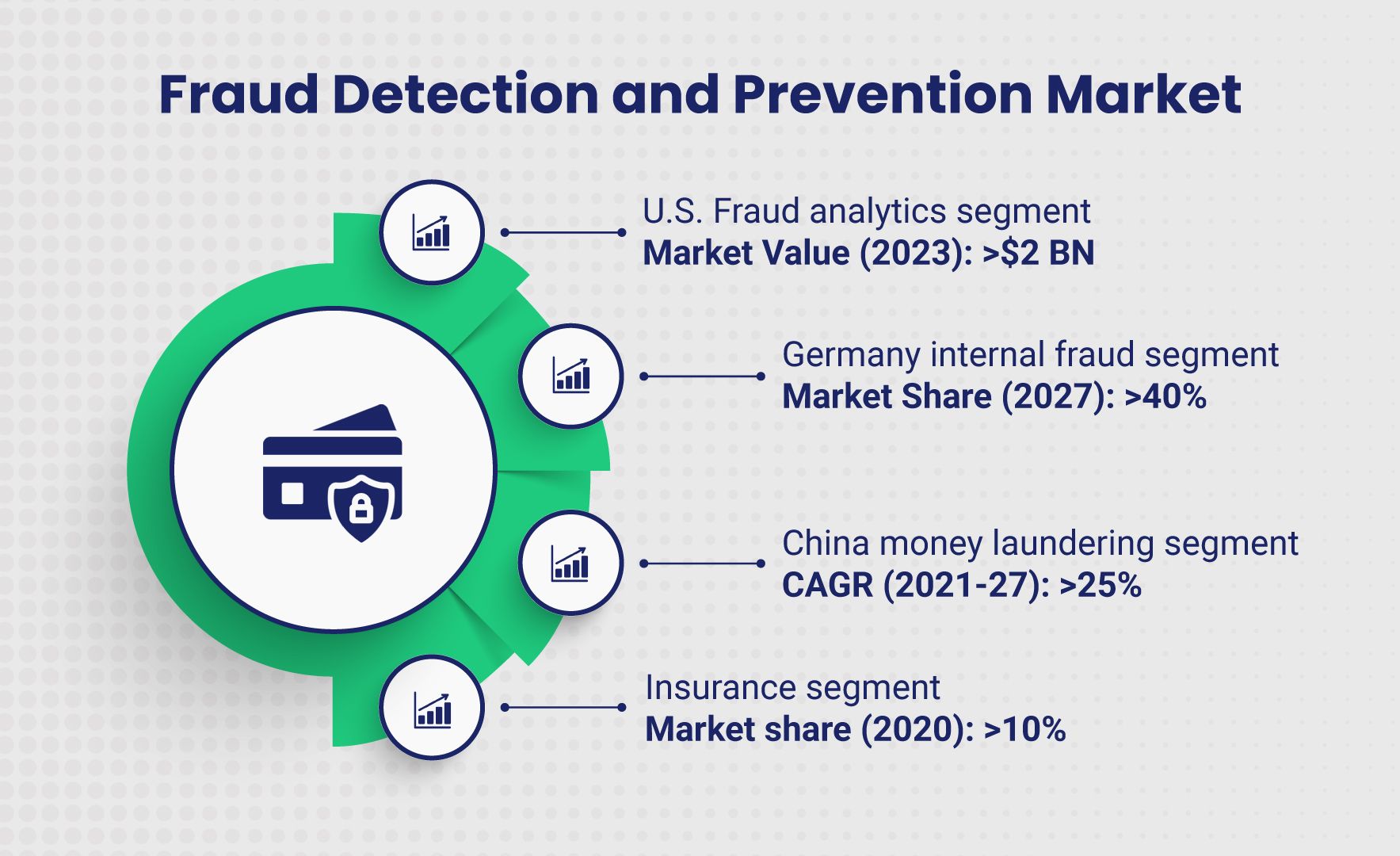
Source: Global Market Insights
How Does Fraud Monitoring Work?
Risk-based fraud monitoring compares each transaction to statistical models and assigns the transaction a risk score. These scores are numeric values that convey the risk associated with a transaction based on data collected from the session, user, device, and more. Organizations can establish different flows for transactions that reach certain risk thresholds, and customize fraud prevention measures to suit their risk tolerance and company policies.
Datasets used to accomplish this can include hundreds of different indicators to identify malicious activity. Increasingly, it also involves cyber-intelligence and takedown services to detect and neutralize fraudsters targeting the organization’s customers outside perimeter defenses. The following are three common forms of fraud monitoring in use today.
Transaction Monitoring
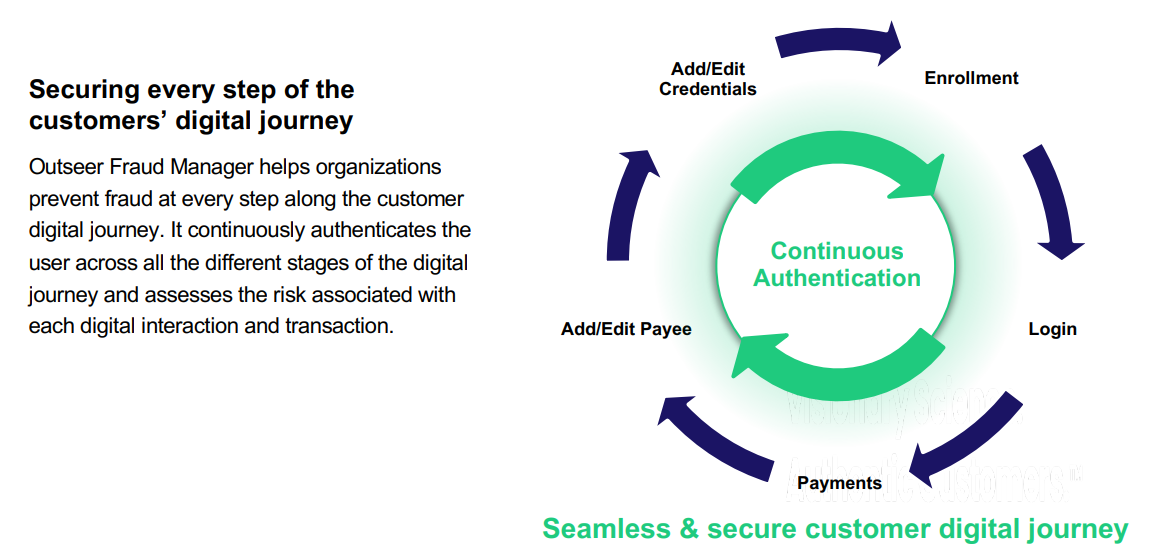
Monitoring each customer transaction is vital for fraud prevention. Machine-learning algorithms are continuously refined to establish what legitimate customer activity looks like in order to instantly surface anomalous behavior that could signal fraud.
Source: Outseer Fraud Manager Solution
Actions such as updating payment information, adding a beneficiary, or changing contact information are also recorded and weighed when assessing risk and uncovering fraudulent trends.
Examples of transactional data can include the following:
- Purchase history
- Transaction amount
- Device IP address
- Geolocation
- Age of the account
Transaction monitoring also uncovers patterns that indicate potential fraud attempts. Understanding these patterns and monitoring for them can help you prevent financial loss and data theft. For instance, the following actions could indicate an account has been compromised:
- A login occurs from a new IP address
- The login does not match the geographical location of previous sessions
- The user checks the account balance
- The user attempts to change the password but cannot
- The user attempts to issue multiple large transactions
The longer transaction monitoring is in place, the better machine learning algorithms will get at identifying fraudulent patterns and delineating those behaviors from legitimate customer activity.
Session Monitoring
Session monitoring uses similar techniques to identity fraud, but it monitors aspects of the user session, whether it’s banking, e-commerce, or any other use case. Each session is monitored individually for abnormal or suspicious behavior. This can both stop fraudulent transactions and help protect legitimate customers from fraudulent purchases or transfers as well as theft of payment details or rewards points.
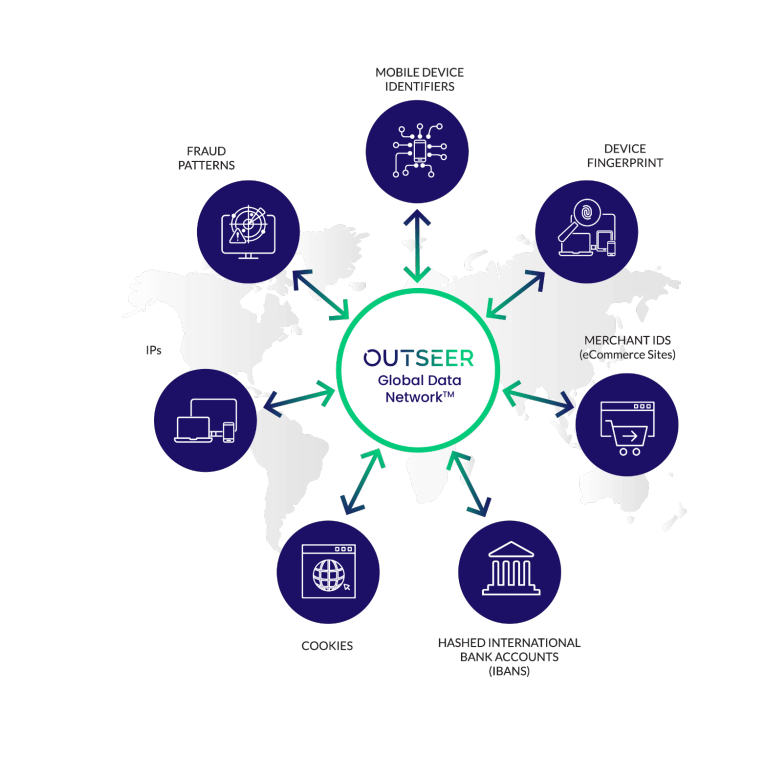
Fraud monitoring can also be used to identify and stop malicious scripts. For example, a fraudster may write a script to automate the process of trying a combination of different passwords for an account. Session monitoring can stop this attack by blocking it outright, or requiring a CAPTCHA check or step-up identity verification.
In another example, session monitoring may detect fraud if the location or type of device changes during the course of the session. A payment initiated in one country but authorized in another would be considered high-risk behavior, for instance.
Additional examples of monitored session data can include the following:
- Typing speed
- Type of browser
- Operating system
- IP address
- Geolocation
Brand Monitoring
Cybercriminals often impersonate trusted brands in order to scam unsuspecting customers. Fraudsters use phishing emails, fraudulent mobile apps, and phony social media pages to hijack a brand’s identity and exploit brand reputation in attacks targeting customers and other consumers and businesses.
Fraud monitoring solutions designed to short-circuit this kind of “brandjacking” employ expert analysis and artificial intelligence to continuously scan the digital landscape for signs of brand impersonation in social media, app stores, and domain registrations and then work to shut them down.
What Happens When Fraud Is Detected?
Transaction & Account Fraud
Different actions and attributes of a login, transaction, or other activity contribute to its overall risk score. Based on an organization’s designated thresholds, a transaction can either be approved, blocked, or sent through a challenge flow depending on the score. Transactions deemed low risk are sent through a frictionless flow, meaning no additional steps or information is required to proceed.
With today’s most sophisticated solutions, challenge flows are initiated for only those rare logins or transactions that truly warrant additional scrutiny. Typically, these challenges require the user to provide additional identity information to complete the login or transaction. This could be a One Time Password (OTP) sent via text or email or even include biometric authentication via fingerprint scan. Challenge flows are only applied to risky transactions, keeping your customers safe and conversion rates high.
Brand Fraud
As soon as fraudulent sites, apps, or social media pages are identified, takedowns are immediately initiated, helping to mitigate cyberattacks before they cause serious harm to customers or to the brand. Brand monitoring providers work directly with platforms and registrars so organizations don’t have to expend the considerable amount of time or resources needed to do this themselves.
What to Look for in Fraud Monitoring Services
Not all fraud monitoring services are created equal. Here are some key features you’ll want to look out for when choosing a fraud monitoring service.
Machine Learning and Data Science Expertise
Leveraging machine learning is critical for modern fraud prevention. This method of detection identifies fraud based on behavior, rather than known attack attributes. For instance, signature-based detection relies on fingerprinting each fraudulent action, with each variation of fraud having its own unique ID. When an attack matches the rule set, it is blocked.
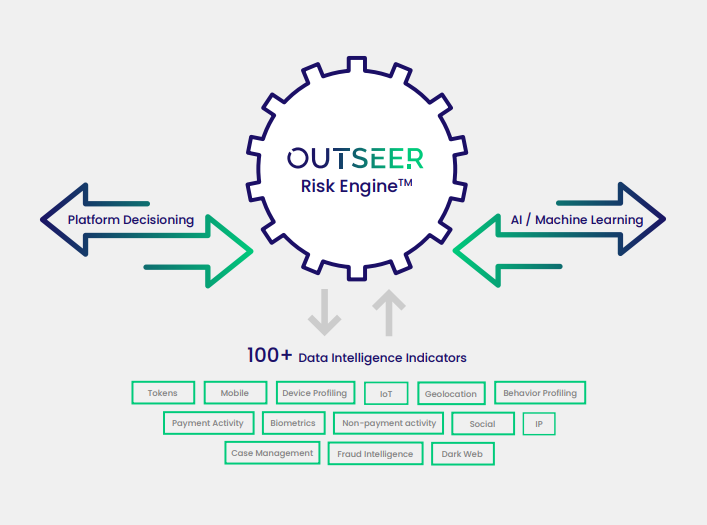
The problem with this method is that it creates massive rule sets that are easy for fraudsters to bypass. If cybercriminals introduce slight variations to their attacks, signature-based monitoring will fail to identify them.
As with all machine learning-based approaches, algorithms are only as good as the size and quality of the underlying dataset and the expertise of the data scientists who train them. As a result, it’s best to source solutions from providers with proven expertise in leveraging global, cross-industry intelligence to differentiate legitimate customers from criminal behavior in real time.
Take our own market-leading anti-fraud products for example. Outseer 3-D Secure builds upon the EMV® 3-D Secure payment standard to deliver unrivalled protection against card-not-present (CNP) fraud. And Outseer Fraud Manager detects and prevents fraud in every customer interaction—including logins, enrollments, in-session activities, and more.
Both are powered by advanced data science informed by shared transaction and identity data from more than 6,500 partners spanning every industry and geography to make faster, smarter risk decisions at every moment.
Frictionless Flow for a Faster, Safer Customer Experience
Stopping transaction fraud shouldn’t have to cost you conversions. Look for products that offer step-up verification with frictionless flow. This protects the customer experience by only requiring additional information for the scant few transactions, logins, or other activities that are truly high risk. Outseer solutions, for instance, prevent 95% of all fraud loss while reserving interventions for a mere 5% of all transactions. That’s the best performance in the industry.
Comprehensive Brand Protection
With phishing attacks on the rise, brand protection is vital to a comprehensive fraud monitoring strategy. Look for fraud monitoring products that offer continuous scanning, phishing protection, and automatic takedown services to protect your brand. Here again, we can help. Outseer FraudAction provides 24/7, all-inclusive threat management to protect your brand and your customers from phishing and malware, fraudulent mobile apps and bogus social media pages.
Seeing What Others Can’t to Protect & Grow Your Business
Mastering the nuances of risk-based fraud monitoring can be daunting for most companies. And building the kind of global, cross-industry data consortium needed to do it right is largely impossible on their own. That’s why major credit card companies, financial services firms, and payment processors source providers like Outseer to protect themselves and the businesses they serve.
Outseer delivers seamless fraud protection that defeats both fraud and user friction at the same time. Through machine learning, data science, and shared global intelligence, our products secure transactions—more than $100 billions worth in just the first half of 2021—and kneecap brand impersonations that threaten financial and reputational harm.
The Best Fraud Management Software
To learn how you can leverage real-time, risk-based fraud monitoring to protect your company and its customers, request a free demo today.