In today’s world, staying one step ahead of scammers and fraud has become more important than ever.
When it comes to card-not-present transactions, there are several types of scams and threats that individuals, financial institutions, and businesses should be aware of.
- Phishing: Scammers send fraudulent emails or messages pretending to be legitimate organisations, tricking individuals into revealing their personal information, such as credit card details or login credentials.
- Identity Theft: Fraudsters steal personal information, such as names, addresses, and credit card numbers, with the intention of using them for unauthorised transactions.
- Account Takeover: Scammers gain unauthorised access to a person’s account and make fraudulent transactions without their knowledge or consent.
- Card Skimming: Criminals use devices to steal credit card information by capturing the card details when it is swiped or entered into compromised payment terminals or websites.
- Man-in-the-Middle Attacks: Hackers intercept communication between the customer and the merchant, allowing them to eavesdrop, modify, or steal sensitive information during the transaction.
- Triangulation Fraud: Customers buy from genuine marketplaces, but scammers are fraudulently selling the items purchased fraudulently from another retailer.
- Card Testing: Fraudsters use automated scripts or software to test stolen credit card numbers on various websites to determine which ones are valid before using them for fraudulent purchases.
- Social Engineering: Scammers manipulate individuals through psychological tactics, persuading them to provide sensitive information or perform actions that benefit the fraudster.
Sometimes, as the Aite Faster Payments, Faster Fraud Report (May 2023) points out, the consumer is the weakest link as fraudsters have developed a tried-and-true playbook and have replicated this attack vector across multiple geographies.
Outseer has seen a significant increase in counterfeit text messages imitating legitimate banks or companies to not only steal consumer data but also even as far as installing malware/ransomware onto the consumer’s device. The type of messages being received by customers are designed to trigger the emotional response to act quickly, either leading to a benefit or risk if the customer was not to act. However, behind the scenes, this is all a front and is used as an incentive to push the customer into sharing information.
The banking, financial services, and insurance industry are directly affected by data breaches from other companies for example, Emma Sleep Company confirmed that it suffered a Magecart attack which enabled ne’er-do-wells to skim customers’ credit or debit card data from its website.
The Power of Outseer 3-D Secure ACS in Combating Card-Not-Present Fraud
Outseer 3-D Secure is a powerful solution that can make a significant difference in the ongoing battle against card-not-present fraud and scams. It provides the tools needed for card issuers to author and manage their 3DS screen text themselves and tailor the text and screens shown based on different types of payments.
Originally this was used to write challenge screens in different languages and to customise the screen text to the needs of each issuer’s own UX requirements. However, the flexibility of Outseer 3DS enabling issuers to self-manage their screens is helping them find new ways to enhance the experience for cardholders and prevent even more fraud.
Customising 3DS Screen Text for Enhanced Cardholder Experience
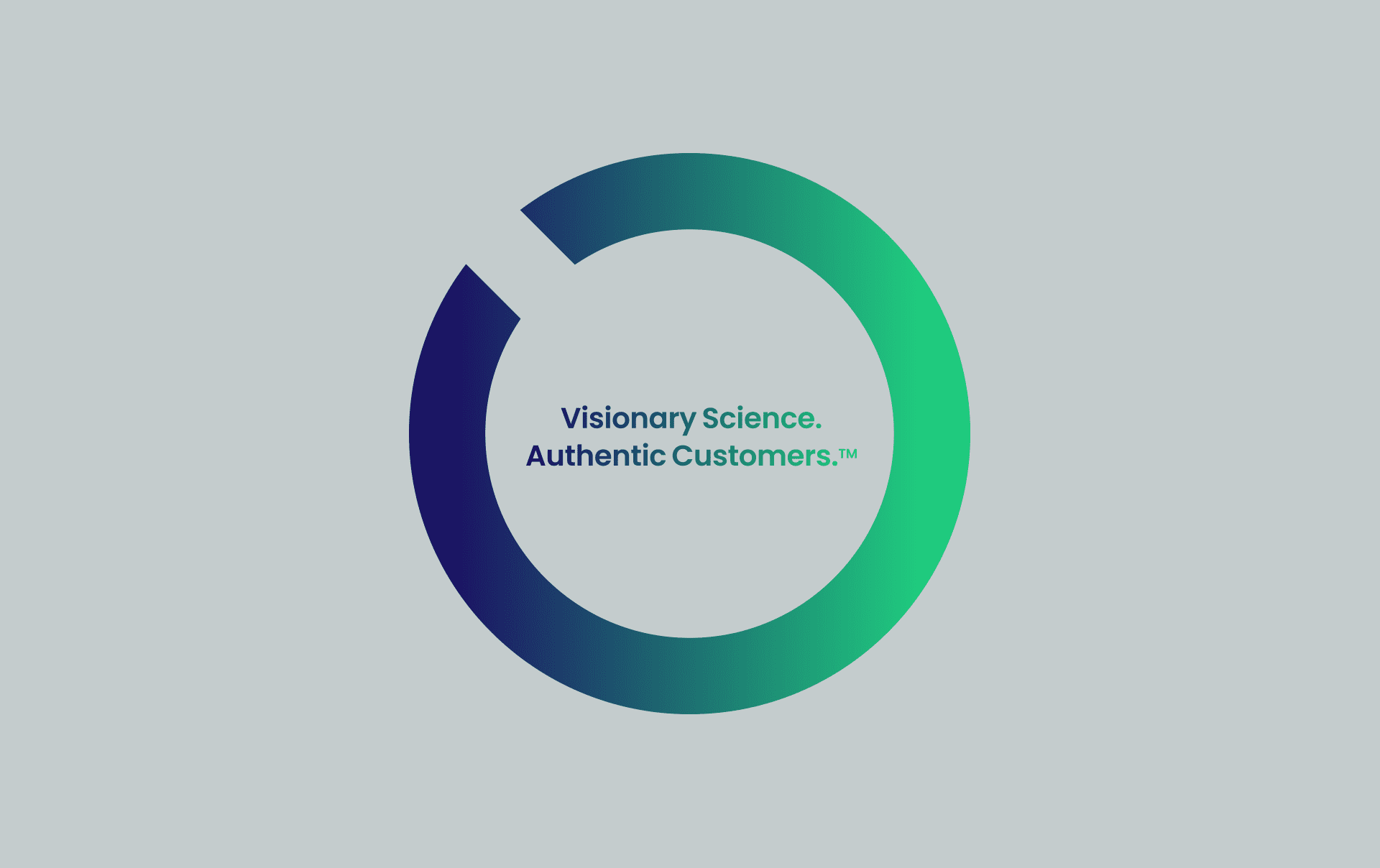
As an example of a better cardholder experience, instead of a generic authentication screen for every transaction type, unique screens can be shown for different payment flows. For example, recurring payments are clearer with specific text outlining that it is a recurring payment.
Example Outseer 3-D Secure Screen for Recurring Transactions
The issuer receives transaction data in real-time, even the full EMV 3DS protocol data elements from the merchant are available for the issuer to process in real-time. This not only gives the issuer the ability to store EMV 3DS transaction data in an issuer data lake for their own BI analysis and reporting, or to consume EMV 3DS authentication data for more accurate authorisation decisions, but it also gives the issuer a wealth of data to make real-time decisions about the EMV 3DS transaction outcome and which screens should be shown to the cardholder.
Tailoring Screens for Different Payment Flow
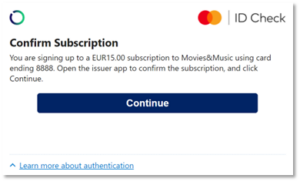
For example, a quasi-cash transaction from a crypto merchant with Merchant Category Code (MCC) 6051 can be identified by the issuer in real-time, and the issuer can make the decision to show a cardholder a different challenge screen based on MCC code and/or merchant name describing the increased risk to the cardholder and remind the cardholder of the risk.
Example screen for a Crypto Transaction
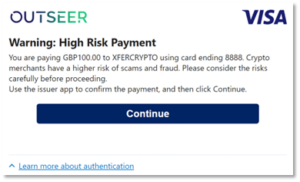
Also, the authentication flow can be different based on real-time issuer decisions. For example, a merchant previously seen in scams could be triggered by the issuer to show an additional warning screen in a mobile app authenticator, it could ask the cardholder additional questions about the transaction – who are they paying, why are they paying, and are they being guided by someone to make the payment.
Example issuer app screen with additional scam warning
Introducing Delays for Increased Cardholder Awareness
Another approach is for the issuer to insert delays into the authentication process to force the cardholder to slow down, take a moment and think about what they are doing before completing the authentication. For example, an issuer using an SMS authentication method for specific higher-risk transactions could first send a warning message, followed a minute later with the challenge code.
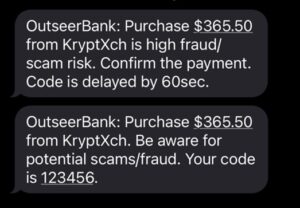
Example delayed SMS
Empowering Issuers with Customised Challenge Screens for Heightened Cardholder Awareness and Fraud Prevention
Combining the proven accuracy of the Outseer Risk Engine with issuer real-time decisions allows issuers to tune the cardholder experience for specific scenarios. A generic authentication screen is not enough to combat scams and is not ideal for different payment flows. Showing the authentication screen too often leads to cardholders becoming too familiar with the challenge flow and becoming complacent about why that challenge screen is being used.
Enabling issuers to be able to select different types of challenge screens only when they match specific high-risk transaction criteria makes the cardholder more aware of their actions and the risk of the payment they are about to approve.
If you require further assistance or want to learn more about fraud prevention strategies, feel free to contact our team at Outseer. Together, we can protect your organisation from the ever-evolving world of fraud.