New NIST Identity Proofing and Authentication ‘Bible’ Out

In August 2025, the US National Institute of Standards and Technology (NIST) has come out with its new standards around authentication and identity proofing. In NIST’s own words:
“These guidelines cover the identity proofing, authentication, and federation of users (e.g., employees, contractors, or private individuals) who interact with government information systems over networks.”
If you are a fraud fighter in any country, this is your go to document to understand the latest in guidance around identity proofing and authentication. NIST has been putting out these documents for several decades. It is probably the best open source for obtaining this unbiased information. NIST is often the first one to call out issues with existing identity proofing and authentication controls. Although these guidance documents are released maybe only every four years, they are packed with the ‘whys’ something must change.
The Four Documents
The first document is NIST SP 800-63-4 Digital Identity Guidelines. This document “describes the digital identity models, risk assessment methodologies and processes for selecting assurance levels for identity proofing, authentication and federation.”
The second document is NIST SP 800-63A-4 Identity Proofing and Enrollment. This document provides “requirements for identity proofing and the remote or in-person enrolment of applicants.” This includes details on the Identity Assurance Levels (IAL) which are used to “convey the degree of confidence that the subject’s claimed identity is their real identity.”
The third document is NIST SP 800-63B-4 Authentication and Authenticator Management. This document provides “requirements for authentication processes that can be used at each of the three AALs (Authentication Assurance Levels), including choice of authenticators.” The AALs levels describe the strength of the authentication.
The fourth document is NIST SP 800-63C-4 Federation and Assertions. This document provides the “requirements on the use of federated identity architectures.” This is more for “the conveyance of identity and authentication information across a set of networked systems.” Unless you are focused on networked systems, you do not need to read this document.
Why is Identity Proofing and Authentication So Important in 2025?
Most financial institutions are using identity proofing and authentication solutions that can be 5–15 years old. Massive new threats to identity proofing and authentication have been introduced by the fraudsters, often sophisticated organized crime or even nation-states. Just think of the new fraudster capabilities from GenAI in the past two years, including agent bots, ability to generate good counterfeit driver’s licenses and passports, ability to defeat liveness testing, better social engineering, etc. Some of these new threats include bypassing multi-factor authentication. In fact, in the UK, the Royal United Services Institute considers “fraud as a national security concern.” A critical amount of fraud originates around weak identity proofing and authentication.
These new threats can make your identity proofing and authentication control stack quite weak.
To select new identity proofing and authentication controls requires a solid framework to help assess what are the critical requirements to mitigate the existing threats. The NIST documents really help solve this need. It took a while for me to find these ‘back in the day’, but once I did, they stayed by my side. It helped to explain to management why our current controls needed updating and the risk if we did not update. As an example, NIST was the first security entity to say stop using OTP email (very insecure) and really consider upgrading away from OTP email (too easy to spoof and the telecom environment was never meant for authentication security). Most financial institutions, and many others, still use OTP, even with these warnings.
What are Examples of What Is Contained in These NIST Guidelines
To help you understand the value of the documents, I will include several really good examples of what you will find in these documents.
Identity Proofing
There is a really good section on threats to identity proofing which include
- Impersonation
- False or fraudulent representation
- Social engineering attacks
- Infrastructure attacks
This section contains examples of these threats and suggested mitigations. Section 3.14 of 800.63A discusses a critical attack vector mitigation, the Presentation Attack Detection (PAD). PAD is automated determination of a presentation attack which interferes with the operation of the biometrics identity proofing.
There is a section of fraud checks that should take place, including:
- Check for recent SIM swaps, and length of time since phone service was activated, on the phone number used as part of the identity process.
- Incorporate device fingerprinting checks to protect against scaled and automated attacks and enrollment duplication.
When confirmation codes are used as part of validating enrollment data, the document provides specifics to the length (minimum 6 digits numeric) and when the code should expire (based on how the code is delivered -e.g. 10 minutes if sent to a validated phone)
There is a section that addresses customer experience to ensure the identity process does not cause customer experience issues.
Authentication
For beginners, the document explains the basics of authenticators:
- Something you know (a password)
- Something you have (a device)
- Something you are (a fingerprint or other biometric)
It cautions that a biometric cannot be used by itself for authentication.
The document explains cryptographic keys and how they can be used. This is a critical component with FIDO authenticators (also discussed in this document).
You often hear of the need for a ‘phishing-resistant’ authenticator to help mitigate phishing attacks and credential theft. Well, Section 3.2.5 of 800-63B will help you understand what ‘phishing-resistant ‘ means and how to make sure you add this control as part of your authenticator solutions.
There is a good section describing Authenticator Assurance Levels (AAL). First is the definition of the three levels:
- AAL1 provides basic confidence the person controls an authenticator
- AAL2 provides high confidence the person controls one or more authenticators
- AAL3 provides very high confidence that the claimant controls authenticators that are bound to the subscriber account.
There is a description of the suggested authenticators for each level and why there may be different levels, even in the same application. See table from the NIST guidance.
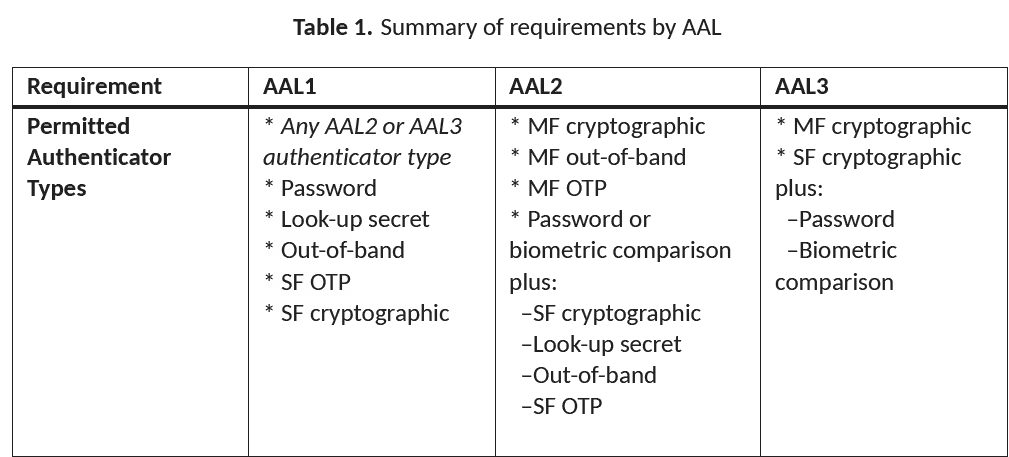
This detailed discussion of Authenticator Assurance Levels and types of authenticators is especially important for EU financial institutions assessing how they will comply with the upcoming PSD3 regulations. Also, articles on PSD3 discuss how financial institutions must include consideration for the vulnerable : “(Strong Customer Authentication) SCA methods must now include authentication ways for vulnerable customers such as the elderly or people with disabilities who don’t rely solely on smartphone access.”
There is a good description of a very detailed point called ‘syncable authenticators’. This where the customer wants to copy the authenticator secret to additional devices. This can be key for customer usability.
There is another good discussion on considering offering multiple authenticators for your customer base. ‘One-size’ authenticator for all customers is no longer a best practice. One key point is to “consider authenticators from the users’ perspective.”
The NIST standards also bring up the important point of “continuous session monitoring.” Section 5.3 of 800-63B talks about the characteristics that can be included, such as behavioral biometrics, device and browser characteristics, usage patterns and velocity.
There is also a threat section on authenticator risks, including device theft, phishing, social engineering, authentication fatigue, unauthorized binding and device sold with keys included.
Final Thoughts
This is a free set of security documents from the US government. It is your primer education on identity proofing and authentication for financial institutions, eCommerce, and more. Read them at your own pace. Print them off and highlight and mark them up. It will be like an old novel you really liked. Or maybe that college textbook that was so well written, it really got you through the course. Your course today is to protect your FI and your customers—and this course does not end. So, buckle up and make the 2025 NIST identity proofing and authentication guidance your new best friend. Enjoy and this will help keep your FI and your customers stay safe.





