In recent times, the rise of Android Banking Trojans has become a cause for concern in the realm of cybersecurity. Threat actors have recognized the lucrative potential of these Trojans and have begun developing and selling customized overlay injections, targeting not only traditional financial institutions but also various other sectors such as cryptowallets, streaming platforms, delivery services, retail stores, and more. This blog delves into the dangers posed by Android Banking Trojans and emphasizes the importance of combating them by terminating their Command & Control (C&C) servers.
The Significance of Command & Control Servers
C&C servers act as the central control hub for Android Banking Trojans, allowing the attackers to remotely manage and control the infected devices. These servers serve as the brains behind the malware, enabling threat actors to execute malicious activities. Some C&C panels may adopt deceptive tactics, such as presenting innocuous blank pages or fake 404 errors, while others employ warnings like “Your connection is not secure.” In certain cases, fraudsters design login panels specifically crafted to facilitate interaction with compromised devices.
Top Three Most Active Android Banking Trojans
- Hydra (formerly known as BianLian): Hydra has emerged as the most widespread Android Banking Trojan in recent months. It offers similar functionalities to other dangerous banking Trojans, but what sets it apart is its continually evolving cookie-stealing feature and its ability to target specific brands. Hydra is offered as Malware as a Service (MaaS) and has dominated the Android Banking Trojan landscape in terms of the number of observed online C&C servers.
- Octo (also known as Coper or ExobotCompact): Octo is a formidable Android Banking Trojan that has gained notoriety within the cybercrime landscape. Like other advanced banking Trojans, Octo is offered as MaaS in underground forums. It possesses anti-analysis techniques and can capture data from other installed apps visible on the infected device’s screen.
- Alien: Alien is a mobile banking Trojan that operates as Malware as a Service (MaaS). It is believed to have derived from the well-known Cerberus banking Android Banking Trojan, which was highly active between 2019 and 2020.
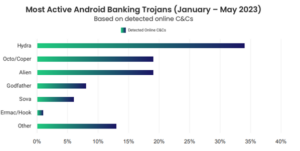
Targeted Apps by Trojan Type and Country
Android Banking Trojans have emerged as a significant threat, impacting a wide range of applications, industries, and regions. Among the top three countries with the highest app injections offered are the United States, the United Arab Emirates (UAE), and the United Kingdom (UK).
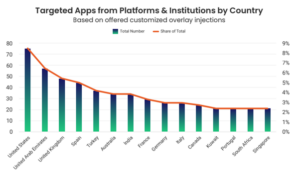
In addition to the specific countries, certain regions have become hotspots for Android Banking Trojan activities. The top three regions with the highest app injections offered include the European Union (EU), the Asia-Pacific and Japan (APJ) region, and the UAE.
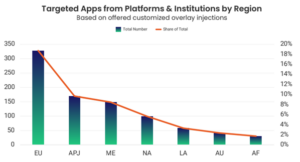
When it comes to industries, the Banking, Financial Services, and Insurance (BFSI) sector bears the brunt of Android Banking Trojans, accounting for a staggering 76% of the total share. This industry is an attractive target due to its wealth of sensitive financial information and the potential for significant financial gains for threat actors. As the backbone of the global economy, the BFSI sector faces constant challenges in securing its mobile banking infrastructure and safeguarding customer data.
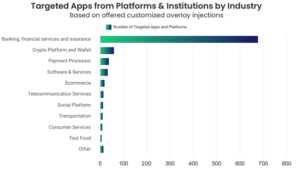
The prominence of the BFSI industry in mobile banking Trojan attacks underscores the need for enhanced security measures and proactive defence strategies. Financial institutions, banks, and insurance companies must prioritize investments in robust fraud prevention solutions and adopt a multi-layered approach to protect their customers and assets. This includes implementing stringent authentication mechanisms, continuously monitoring for unusual activities, and educating users about potential risks and best practices.
However, it is important to note that Android Banking Trojans do not discriminate when it comes to their potential targets. While the BFSI industry may be the primary focus, other sectors, such as healthcare, e-commerce, and entertainment, also face risks. Threat actors have expanded their scope and are increasingly targeting non-traditional banking companies, including streaming platforms, delivery services, retail stores, and gasoline apps. This wide array of targeted industries highlights the versatility and adaptability of Android Banking Trojans.
Combating Android Banking Trojans: The Role of C&C Server Takedowns
The hunt for C&C servers plays a critical role in combating the threat Android Banking Trojans pose. Detecting and dismantling these malicious servers is crucial to minimizing and preventing the damage caused by Trojans, safeguarding both individual users and organizations.
The increasing prevalence of Android Banking Trojans and the sale of customized overlay injections highlight the pressing need for robust cybersecurity measures. As threat actors continue to evolve their tactics and target various sectors, it becomes essential for users and organizations to remain vigilant and take proactive steps to protect themselves. By focusing on identifying and eliminating Command & Control servers, we can significantly mitigate the damage caused by these Trojans and ensure a safer digital landscape for everyone involved.
If you require further assistance or want to learn more about fraud prevention strategies, feel free to contact our team at Outseer. Together, we can protect your organization from the ever-evolving world of fraud.