Introduction
Over the last months of 2023, a notable event has taken place in the realm of mobile malware — the complete leak of the Hook Android banking trojan’s APK and Panel source code. This significant development is not only shaping the current landscape but also holds implications that are about to influence the future of Android banking trojans.
Brief History
In January 2023 a known actor nicknamed “DukeEugene” advertised the renting services of a new software targeting Android devices. This software was later that month reported by ThreatFabric and dubbed as “Hook”.
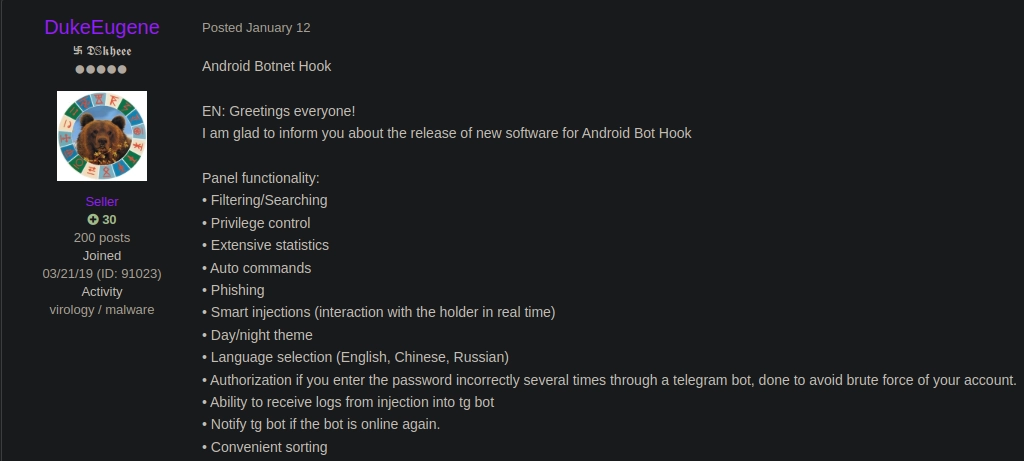
Post in fraud forum Translated from Russian by DukeEugene advertising Hook
Hook is an Android banking trojan a direct descendant of the “Ermac” banking trojan designed to steal financial and personal information from mobile devices running the Android operating system. Armed with advanced capabilities, Hook encompasses contact harvesting, SMS interception, keylogging, capture 2FA, RAT capabilities, overlay injection, and more.
One of the key aspects of the Hook and Android banking trojans in general, is the communication established between infected devices and the centralized or decentralized servers known as Command-and-Control Servers (C&Cs or C2). This gives malware operators the ability to receive information on infected devices and execute additional commands remotely.
Outseer FraudAction ATS (Anti Trojan Service) team constantly monitors these C&Cs. Notably, for the first half-year of 2023, the number of active Hook C&C servers remained relatively low compared to other well-known banking trojans like Alien, Hydra, and Octo. For a detailed exploration of the first half of 2023, please refer to Hunting The Command & Control Servers: Android Banking Trojans In the First Half of 2023.
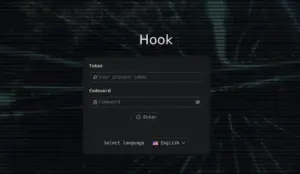
Hook C&C Panel
In April 2023 DukeEugene announced that he was leaving for military service and is closing the Hook project. However, the project’s coder, known as ‘RedDragon,’ has continued to provide services for existing customers.”
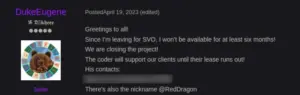
DukeEugene advertising that the project is closed translated from Russian
Fast forward three months to July 2023, a threat intelligence researcher known as “0xperator” tweeted that the HookBot builder panel code had been leaked. However, at that time, certain features were notably absent. It wasn’t until the 30th of October that the entire code was fully leaked.
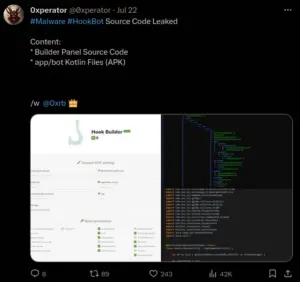
0xperator tweet of HookBot leaked source code
User discussing recent leaks in fraud forum
The source code leaked allows malware operators to set up and run the C&C server on a publicly available address and create a Hook malware App disguised as a legitimate-looking application in a matter of minutes. The App created has the necessary functionalities to communicate with the created C&C server. As a result, the malware operator can now focus primarily on spreading the malware.
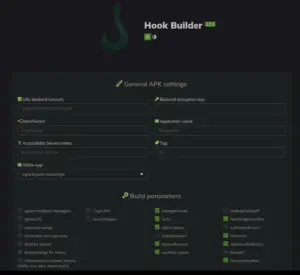
Hook Builder Panel
These events led to massive growth in HookBot C&Cs with over 200 new C&Cs detected in the last couple of months of 2023. With intermediate tech knowledge and without the burden of rental fees, fraudsters now have the option to utilize Hook as a tool for carrying out fraudulent activities. Notably, not only have ‘newcomers’ adopted Hook, but we’ve also identified customized variants of HookBot panels and their favicon web titles that bear a resemblance to the names of well-known groups and threat actors who typically employ other types of malwares.
Customized Hook panels and Hook panel titles
While we cannot confirm a definitive link between the identified resembling names and their associated actors, one case did catch our attention as particularly interesting. We’ve observed a pattern where various Hook samples, named ‘MOD’ or ‘Мод,’ share identical app icons and exclusively communicate with C&C panels featuring the name MOD. This distinctive name and icon correspond precisely to the app icon and name that an actor we name “7key7″* has been using for years while operating or renting this version of Cerberus malware.
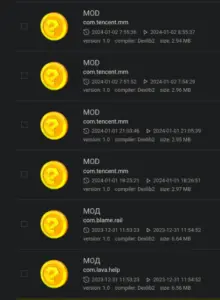
List of malicious APK samples named MOD and Мод
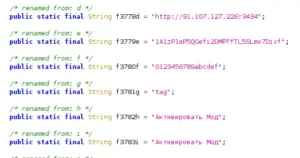
Hook MOD payload configured to a MOD C&C panel address.
Another distinctive trait that led us to suspect that 7key7 has begun utilizing Hook is the absence in use of the overlay injection feature in both the Cerberus and Hook C&C servers operated by 7key7, distinguishing them from the rest of the Hook and Cerberus-related C&Cs.
By default, Hook has over 750 injections at its disposal, where infected devices overlay a fake interface of a targeted brand onto the legitimate app to deceive users into entering their sensitive financial information, targeting different brands worldwide. Moreover, the malware operator can add customized injections if desired. (Contact Outseer to see if your brand is on the targeted list)
Proactive Approach to Safeguard against Future Hook Variants
The threat posed by Android banking trojans continues to grow, with new variants emerging annually. The story of Hook is far from concluded. As both emerging and established actors increasingly leverage Hook to pursue fraudulent objectives, Outseer anticipates seeing new variants based on Hook in the future, each potentially endowed with enhanced functionalities and more dangerous capabilities. It is crucial to hunt, detect, and terminate these malicious servers. With over 20 years of experience and collaborative efforts with various web entities, FraudAction is equipped to swiftly terminate the threat and protect users and organizations from the damaging consequences of Android banking trojans.
IOCs
hxxp://154[.]61[.]74[.]33
hxxp://5[.]35[.]99[.]214
hxxp://91[.]107[.]127[.]226
MD5: 09d910a4370ca19bad8fdb6f34f8abeb
Reference
https://www.threatfabric.com/blogs/hook-a-new-ermac-fork-with-rat-capabilities
https://twitter.com/0xperator/status/1682779709468295168
*7key7 is used as the RC4 key in the encrypted communication in most of the Cerberus samples related to this actor